Serwer "chodzi" na ostatniej możliwej dystrybucji systemu.
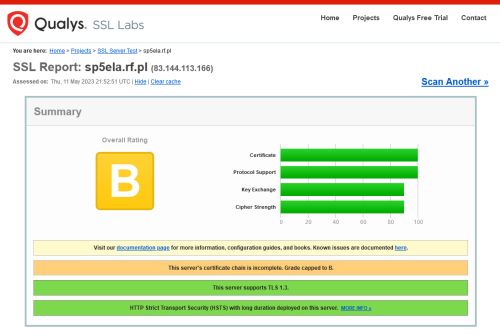
Etap przejściowy instalacji certyfikatu, bez certyfikatu pośredniego (Intemediate Certificate Global Sign). Uzyskana Klasa "B" (Tylko eksperyment).
Klasa certyfikatu (efektywna) zależy od wielu czynników. Systemu operacyjnego, jego konfiguracji, konfiguracji sieciowej, zaimplementowanych protokołów, kompromisu pomiędzy bezpieczeństwem protokołów, a jakością terminali użytkowników oraz innych parametrów.
*Do badań wykorzystano system portalowy firmy Qualsys SSL Labs.
Administratorzy Warsaw DX Club SP5PBE
Dodatek - prace nad konfiguracją certyfikatu SSL/TLS.
Chain issues show "Contains Anchor" when scanning through SSL Labs
Chain issues show "Contains Anchor" when scanning through SSL Labs
It means that you have added Intermediate as well as Root CA, when you only need the Intermediate as the client will already have Root CA (will be already trusted by browser in browser certificate store).
You can get the same info using openssl command:
echo "" | openssl s_client -connect test.stomt.com:443 2>&1 | grep -A 6 "Certificate chain"
It's not an issue in the sense that the anchor is not allowed, but that the extra certificate (which serves no purpose) is increasing the handshake latency.
Because of TCP slow start, the first bytes on a connection are the slowest. Hence, you can minimize the size of the handshake so that HTTP bytes can start flowing as soon as possible. So the issue is not so much "can the extra certificate fit into the initial window" (it most likely can, even with the old setting of 3 network segments), but "what other, more useful, data could we be sending instead".
However, there is no security risk with "Contains anchor", you can largely ignore the "Contains Anchor" warning. Fixing it would possibly save bandwidth slightly and increase the performance.
Source: https://success.qualys.com/support/s/article/000003197
sp5ela







